|
| [Courtesy: Android Authority] |
Abstract:
Ever since the creation of computers, people have been distributing software to avoid paying money or paying to distribute something that people don't want. Pirated Applications and Spam are two primary means to distribute viruses, malware, and worms. Baby steps against these on-line monsters are occasionally made.
In Review: 2013
From January to November last year, nearly 2 viruses, trojans, or generic malware was discovered each month in the Android mobile application market. December had a couple more discovered. For the malware discovered, there are countless numbers of mobile applications which have not yet been discovered... to steal credit card information, identities, or even "command and control" applications to turn your mobile device into a robot against unsuspecting targets (while you pay for the data traffic that is produced!)
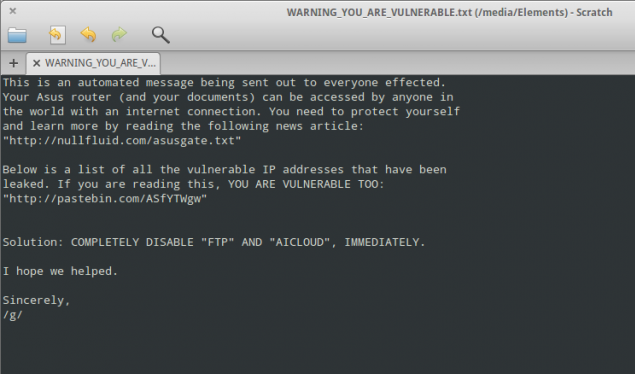
Starting: 2014
While consolidating a list of mobile malware in the Android market was not completed, it is clear that there is some progress in this space... no matter how small.
2014-03-25 U.S. Government First Convictions Over Pirated Mobile Android Applications
The US has enforced its first convictions for illegally distributing counterfeit mobile apps, after two Florida men pleaded guilty for their part in a scheme that sold pirated apps with a total retail value of more than $700,000. Thomas Allen Dye, 21, and 26-year-old Nicholas Anthony Narbone both pleaded guilty to the same charge - conspiracy to commit criminal copyright infringement - earlier this month and are due to be sentenced in June and July respectively. Both men were in the Appbucket group, of which Narbone was the leader, which made and sold more than a million copyrighted Android mobile apps through the group's alternative online market.
2014-03-26 Chinese Arrest 1,500 in Fake Cellular Tower Text Message Spam Raid
China’s police have arrested over 1,500 people on suspicion of using fake base stations to send out mobile SMS spam. The current crackdown, began in February, according to Reuters. Citing a Ministry of Public Security missive, the newswire says a group operating in north-east Liaoning province, bordering North Korea, is suspected of pinging out more than 200 million spam texts.
In Conclusion:
Be diligent! Remember to purchase your applications from reputable places, don't be seduced into stealing applications on-line or purchasing them under list price. Being a thief could make you a victim!