RIM: Unbelievably Down, Unbelievably Long
RIM: Unbelievably Down, Unbelievably Long
Abstract:Sun had a saying "The Network is The Computer". When a network is down, the computer is nearly useless. RIM is now experiencing "The Network is The BlackBerry". The BlackBerry is pretty much useless without the network. The impact to the market may be terrible.
A Short History:Apple had made an attempt to build a "Personal Digital Assistant" market in 1987. The "Newton" seemed to target educators and students. Some other vendors released competing products, but none of them seem to be successful. It was a product "before it's time".
In 1996, U.S. Robotics created the "Palm Pilot", new digital assistant. This became successful, the technology moved to 3Com, Handspring, Palm.
Nokia started the merging of personal digital assistant software into the phone in the late 1990's, later on with some weak web browsing capability. Nokia cobbled together their phone with HP's software. The term "smart phone" was created. Ericson released a concept PDA and phone in 1997 with the eventual culmination of a touchscreen "smartphone" in 2000. The phone used the SymbianOS.
 [2008-2009 Market Trend]
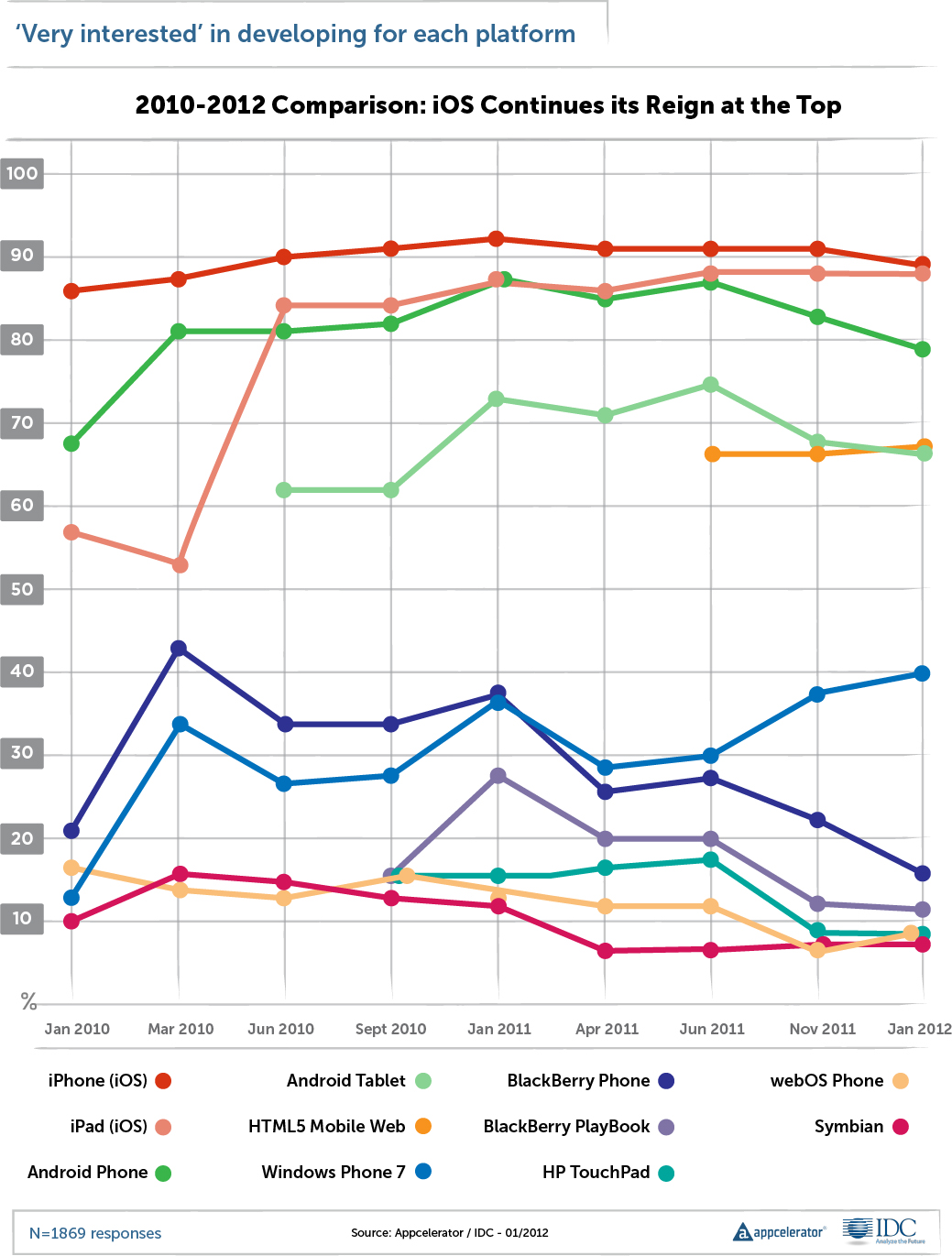
[2008-2009 Market Trend]RIM seems to have virtually created the "smart phone" market in 1999. The merging of digital personal assistant and cell phone seemed to drive their success. Their primary target community was business and financial segments, who could afford an uplifted phone cost for the side benefit of becoming more efficient. The product offering was a success.
 [2006-2009 Market Trend]
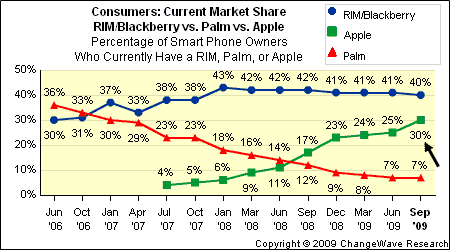
[2006-2009 Market Trend]In the early 2000's, Palm released a merged their personal digital assistant with cell phone technology. The "smart phone" market had a new competitor. Eventually, the technology was purchased by HP, where it resides today.
 [2009-2010 Market Trend]
[2009-2010 Market Trend]Apple computer started designing the iPhone in 2005 and released it in January 2007. Their new "smart phone" (i.e. iPhone), which was speculated to be a "flop" since it did not come with a keyboard. The product targeted the "creative" and "youth" segments, merging functionality from their wildly popular iPod portable music & video playing devices. Also bundled was the first real web browser - until this point, internet HTTP experience was poor. The product offering was a success and placed pressure on RIM by slowly intruding into the business and financial sectors, while other vendors (like Palm and Microsoft) were getting devastated.
 [2010-2011 Market Trend]
[2010-2011 Market Trend]Google started a parallel track to Apple. They purchased Android, Inc in late 2005 and eventually released an operating system called "Android" in late 2007, after the wildly successful Apple iPhone introduction earlier that year. Phone manufacturers jumped on-board Android, trying to get a chunk of the "smart phone" market, without the heavy investment and innovation performed by companies like Palm, RIM, and Apple.

Cell phone giant, Nokia, had been losing market share. Microsoft had been losing marketshare in the mobile phone operating system market. These
two shrinking titans agreed in April 2011 to combine forces - Nokia providing hardware with Microsoft's OS. It could stem the bleeding from both companies or the two shrinking titans might become one sinking titanics.
The Nightmare ScenarioRIM had "secret sauce" embedded into it's BlackBerry communicator - all communciation from their phones were carried over their network infrastructure, in addition to the telephone carrier's infrastructure. RIM's encrypted network allowed them to provide add-on services, as well as security to their business users.
This week, there has been a
multi-day outage for BlackBerry users, across the globe. The problem was with a switch in THEIR INFRASTRUCTURE - which means it is not the fault of a telephone company. Only BlackBerry users are affected - while the rest of the SmartPhone market is unaffected.
Don't Lie To The CustomerRIM's "
secret sauce" is appearing to be their "
achilles heel". Without RIM and their network, the BlackBerry is pretty much useless.
This very week, there is BlackBerry training happening in my corporate headquarters, and when questions regarding the BlackBerry difficulties came up - the trainer said "there must be something wrong with your company's network."
The truth is not only out, but it appears the issue is isolated to THEIR customer network.
Bad DiscusssionsWhen investors and analysts start to talk about situations like these, the language does not get any worse than this.
Jefferies analyst Peter Misek crushed RIM in a research note today. His memo to activists was that RIM's turnaround will take a long time...
Specifically, Misek said that RIM can't be broken up until its migration to QNX is complete in roughly six months. Meanwhile, a management change is difficult. Motorola Mobility CEO Sanjay Jha would be a candidate to lead RIM, but he's highly thought of at Google. Other executives at Apple and Microsoft are largely locked up from going to RIM. PC makers, smartphone rivals, and other takeover options look slim.
Add it up and RIM's only real option at the moment is to execute well and bolster momentum for the BlackBerry. The outages aren't helping that cause.
Surviving because there are no other options on the table when investors are thinking about chopping your comany up into little pieces it not a good place to be.
 When Sharks Attack
When Sharks AttackDuring this very week, Apple had announced their long-anticipated iPhone 4S, a faster SmartPhone with build-in "Cloud Syncronization" - Apple will no longer require a user to have a computer in order to keep their phones backed up or syncronized with music. Apple's phone will no longer require Apple or a PC in order to get the full functionality of it. Apple's open-sourced MacOSX based iPhone was poised for serious growth, without the BlackBerry disaster.
Google is about to feed the market, with it's army of hardware manufacturers, with more open-sourced Android phones while sinking-faster-than-a-brick Nokia and Microsoft are trying to establish a new marketplace with Microsoft's closed-source operating system. Microsoft, with their business relationships, may actually float Nokia, with this unfortunate BlackBerry disaster.
This will surely be a feeding frenzy for the three major remaining phone operating system vendors.
 Bad for the Free Market
Bad for the Free MarketThe Free Market is all about choice - the loss of any major competitor in the market is bad for all of the consumers.
One might argue that RIM's "monopoly" of providing THE centralized infrastructure for all BlackBerries to traverse is the due penalty for their anti-capitalistic tendencies... and their customers deserve what they get for placing all their "
eggs in one basket".
This author is not interested in seeing the diverse market competitors become centralized, since the evil is self-evident, it is dangerous for innovation. There must be freedom to innovate in the highly government regulated market of telecommunications.
Network ManagementThe probable decline of RIM is due to one massive network infrastructure error.
Had their network been better managed, their future decline may not be so sure.
It is possible that they will recover, but I would hate to be in that company today, and I would hate to be the team managing that network today.
The network is the rise and fall of a company - don't mis-manage your network.