Making Known the Secrets to Network Management. Raising up a new generation of professionals.
Sunday, February 24, 2019
DoD: Security Technical Implementation Guides (STIGs)
Friday, May 18, 2018
Meltdown - SPARC Solaris: The Only Safe Choice
Meltdown - SPARC Solaris: The Only Safe Choice
Abstract:
As the rest of the industry has been struggling with security vulnerabilities, SPARC Solaris platforms have been relatively quiet. Meltdown, otherwise known as CVE-2017-5754, has taken the world by storm. Operating Systems have long relied on Memory Management Units to isolate user application programs from the OS kernel. This had come to a screeching halt, leaving lesser secure systems in a world of hurt. |
| [Meltdown Logo, courtesy solaris.wtf] |
Meltdown Vulnerability:
Some OS's will keep the Kernel Pages mapped into the same context as User Application Pages. This is often done for speed (i.e. linux) but places extra dependencies upon the MMU for isolation. Nearly all OS's had ceded this security concern to the CPU vendor, instead of applying the most secure practice in the OS architecture.Meltdown:
As one vendor noted, SPARC Solaris is immune from Meltdown and about the only platform not subject to this critical vulnerability in the data center. This was accomplished by OS designers placing Kernel and User pages into different contexts, a design which added additional security, but at a performance cost that other OS designers in the industry were not willing to cede.Conclusion:
Some Solaris systems, decades ago, may be affected, but nothing modern. Secure by Design is a typical decision for Solaris architects, a decision that has served them well for the decades they served a 64 bit OS to the user community, as other OS vendors played "catch up" in performance or features or functionality.Tuesday, March 31, 2015
Security: 2015q1 Concerns
Viruses, Worms, Vulnerabilities and Spyware concerns during and just prior 2015 Q1.
- [2015-03-07] Litecoin-mining code found in BitTorrent app, freeloaders hit the roof
"μTorrent users are furious after discovering their favorite file-sharing app is quietly bundled with a Litecoin mining program. The alt-coin miner is developed by distributed computing biz Epic Scale, and is bundled in some installations of μTorrent, which is a Windows BitTorrent client. Some peeps are really annoyed that Epic's code is running in the background while they illegally pirate torrent movies and Adobe Creative Suite Linux ISOs, and say they didn't ask for it to be installed."
- [2015-03-06] FREAKing HELL: All Windows versions vulnerable to SSL snoop
"Microsoft has confirmed that its implementation of SSL/TLS in all versions of Windows is vulnerable to the FREAK encryption-downgrade attack. This means if you're using the firm's Windows operating system, an attacker on your network can potentially force Internet Explorer and other software using the Windows Secure Channel component to deploy weak encryption over the web. Intercepted HTTPS connections can be easily cracked, revealing sensitive details such as login cookies and banking information, but only if the website or service at the other end is still supporting 1990s-era cryptography (and millions of sites still are)."
- [2015-03-05] Broadband routers: SOHOpeless and vendors don't care
"Home and small business router security is terrible. Exploits emerge with depressing regularity, exposing millions of users to criminal activities. Many of the holes are so simple as to be embarrassing. Hard-coded credentials are so common in small home and office routers, comparatively to other tech kit, that only those with tin-foil hats bother to suggest the flaws are deliberate." - [2015-03-05] Obama criticises China's mandatory backdoor tech import rules
"US prez Barack Obama has criticised China's new tech rules, urging the country to reverse the policy if it wants a business-as-usual situation with the US to continue. As previously reported, proposed new regulations from the Chinese government would require technology firms to create backdoors and provide source code to the Chinese government before technology sales within China would be authorised. China is also asking that tech companies adopt Chinese encryption algorithms and disclose elements of their intellectual property." - [2015-03-05] Sales up at NSA SIM hack scandal biz Gemalto
"Sales at the world's biggest SIM card maker, Gemalto, which was last month revealed to have been hacked by the NSA and GCHQ, rose by five per cent to €2.5bn (£1.8bn) in 2014. Following the hack, the company's share price fell by $470m last month. In February, it was revealed that the NSA and Britain's GCHQ had hacked the company to harvest the encryption keys, according to documents leaked by former NSA sysadmin, whistleblower Edward Snowden."
- [2015-02-24] SSL-busting adware: US cyber-plod open fire on Comodo's PrivDog
"Essentially, Comodo's firewall and antivirus package Internet Security 2014, installs a tool called PrivDog by default. Some versions of this tool intercept encrypted HTTPS traffic to force ads into webpages. PrivDog, like the Lenovo-embarrassing Superfish, does this using a man-in-the-middle attack: it installs a custom root CA certificate on the Windows PC, and then intercepts connections to websites. Web browsers are fooled into thinking they are talking to legit websites, such as online banks and secure webmail, when in fact they are being tampered with by PrivDog so it can inject adverts. If that's not bad enough, PrivDog turns invalid HTTPS certificates on the web into valid ones: an attacker on your network can point your computer at an evil password-stealing website dressed up as your online bank, and you'd be none the wiser thanks to PrivDog." - [2015-02-23] Psst, hackers. Just go for the known vulnerabilities
"Every one of the top ten vulnerabilities exploited in 2014 took advantage of code written years or even decades ago, according to HP, which recorded an increase in the level of mobile malware detected. “Many of the biggest security risks are issues we’ve known about for decades, leaving organisations unnecessarily exposed,” said Art Gilliland, senior vice president and general manager, Enterprise Security Products, HP. “We can’t lose sight of defending against these known vulnerabilities by entrusting security to the next silver bullet technology; rather, organisations must employ fundamental security tactics to address known vulnerabilities and in turn, eliminate significant amounts of risk," he added."
 |
| [Chinese Virus Image, courtesy WatchChinaTimes.com] |
- [2015-02-20] So long, Lenovo, and no thanks for all the super-creepy Superfish
"Chinese PC maker Lenovo has published instructions on how to scrape off the Superfish adware it installed on its laptops – but still bizarrely insists it has done nothing wrong. That's despite rating the severity of the deliberate infection as "high" on its own website. Well played, Lenonope. Superfish was bundled on new Lenovo Windows laptops with a root CA certificate so it could intercept even HTTPS-protected websites visited by the user and inject ads into the pages. Removing the Superfish badware will leave behind the root certificate – allowing miscreants to lure Lenovo owners to websites masquerading as online banks, webmail and other legit sites, and steal passwords in man-in-the-middle attacks."
- [2015-02-15] Mozilla's Flash-killer 'Shumway' appears in Firefox nightlies
"Open source SWF player promises alternative to Adobe's endless security horror. In November 2012 the Mozilla Foundation announced “Project Shumway”, an effort to create a “web-native runtime implementation of the SWF file format.” Two-and-a-bit years, and a colossal number of Flash bugs later, Shumway has achieved an important milestone by appearing in a Firefox nightly, a step that suggests it's getting closer to inclusion in the browser. Shumway's been available as a plugin for some time, and appears entirely capable of handling the SWF files."
- [2015-01-29] What do China, FBI and UK have in common? All three want backdoors...
"The Chinese government wants backdoors added to all technology imported into the Middle Kingdom as well as all its source code handed over. Suppliers of hardware and software must also submit to invasive audits, the New York Times reports. The new requirements, detailed in a 22-page document approved late last year, are ostensibly intended to strengthen the cybersecurity of critical Chinese industries. Ironically, backdoors are slammed by computer security experts because the access points are ideal for hackers to exploit as well as g-men."
- [2015-01-15] Console hacker DDoS bot runs on lame home routers
"Console DDoSers Lizard Squad are using insecure home routers for a paid service that floods target networks, researchers say. The service crawls the web looking for home and commercial routers secured using lousy default credentials that could easily be brute-forced and then added to its growing botnet. Researchers close to a police investigation into Lizard Squad shared details of the attacks with cybercrime reporter Brian Krebs. The attacks used what was described as a 'crude' spin-off of a Linux trojan identified in November that would spread from one router to another, and potentially to embedded devices that accept inbound telnet connections. High-capacity university routers were also compromised in the botnet which according to the service boasted having run 17,439 DDoS attacks or boots at the time of writing."
- [2014-12-14] CoolReaper pre-installed malware creates backdoor on Chinese Androids
"Security researchers have discovered a backdoor in Android devices sold by Coolpad, a Chinese smartphone manufacturer. The “CoolReaper” vuln has exposed over 10 million users to potential malicious activity. Palo Alto Networks reckons the malware was “installed and maintained by Coolpad despite objections from customers”. It's common for device manufacturers to install software on top of Google’s Android mobile operating system to provide additional functionality or to customise Android devices. Some mobile carriers install applications that gather data on device performance. But CoolReaper operates well beyond the collection of basic usage data, acting as a true backdoor into Coolpad devices - according to Palo Alto.CoolReaper has been identified on 24 phone models sold by Coolpad."
- [2014-11-24] Regin: The super-spyware the security industry has been silent about
"A public autopsy of sophisticated intelligence-gathering spyware Regin is causing waves today in the computer security world... On Sunday, Symantec published a detailed dissection of the Regin malware, and it looks to be one of the most advanced pieces of spyware code yet found. The software targets Windows PCs, and a zero-day vulnerability said to be in Yahoo! Messenger, before burrowing into the kernel layer. It hides itself in own private area on hard disks, has its own virtual filesystem, and encrypts and morphs itself multiple times to evade detection. It uses a toolkit of payloads to eavesdrop on the administration of mobile phone masts, intercept network traffic, pore over emails, and so on... Kaspersky's report on Regin today shows it has the ability to infiltrate GSM phone networks. The malware can receive commands over a cell network, which is unusual."
Sunday, March 8, 2015
Security: SuperFish and HeartBleed Vulnerabilities
Some Nice Security Testers...
There has been a lot of security discussion lately, regarding SSL. Both SuperFish corporation and HeartBleed vulnerability have been in the cross-hairs.
 |
| [Dead Fish on Beach, courtesy Wikipedia] |
Detecting a SuperFish Issue...
While SuperFish is not strictly a vulnerability, the poor security policy can allow for the bypass SSL security.
Filippo.IO was kind enough to assemble a SuperFish vulnerability tester - go and test your PC here!
Detect a Bleeding Heart...
If you have a web site you commonly use, Filippo.IO also offers a HeartBleed vulnerability tester.
Sunday, April 13, 2014
Security: Heartbleed, Apple, MacOSX, iOS, Linux, and Android
Abstract:
Nearly every computing device today is connected together via a network of some kind. These connections open up opportunities or vulnerabilities for exploitation by mafia, criminals, or government espionage via malware. While computers such as MacOSX are immune, along with their mobile devices based upon iOS iPhone and iPads... huge numbers of Linux and Android devices are at risk!
Heartbleed:
This particular vulnerability can be leveraged by many sources in order to capture usernames and passwords, where those account credentials can be later used for nefarious purposes. Nefarious includes: command and control to attack commercial, financial, government, or even launch attacks against entire national electrical grids; stealing money; stealing compute resources. The defect is well documented.
Apple and Android/Linux Vulnerabilities:
There are many operating systems which are vulnerable to this defect, but for this article, we are only really concerned about the mobile market.
While most of the buzz surrounding OpenSSL's Heartbleed vulnerability has focussed on websites and other servers, the SANS Institute reminds us that software running on PCs, tablets and more is just as potentially vulnerable.
Williams said a dodgy server could easily send a message to vulnerable software on phones, laptops, PCs, home routers and other devices, and retrieve up to 64KB of highly sensitive data from the targeted system at a time. It's an attack that would probably yield handy amounts of data if deployed against users of public Wi-Fi hotspots, for example.
While Google said in a blog post on April 9 that all versions of Android are immune to the flaw, it added that the “limited exception” was one version dubbed 4.1.1, which was released in 2012.
Security researchers said that version of Android is still used in millions of smartphones and tablets, including popular models made by Samsung Electronics Co., HTC Corp. and other manufacturers. Google statistics show that 34 percent of Android devices use variations of the 4.1 software.
The company said less than 10 percent of active devices are vulnerable. More than 900 million Android devices have been activated worldwide.
After taking a few days to check its security, the fruity firm joined other companies in publicly announcing how worried or secure its customers should feel.
“Apple takes security very seriously. IOS and OS X never incorporated the vulnerable software and key Web-based services were not affected,” an Apple spokesperson said.
Conclusions:
To give an adequate understanding regarding the number of mobile Android devices at risk, one could take the population of the United States, at roughly 317 Million people as a baseline. 90 million Android Linux based devices vulnerable, that is equivalent to nearly 28% of the population of the United States is at risk! This is no small number of mobile devices - there is a lot of patching that either needs to be done or mobile devices which should be destroyed. Ensure you check your android device!
Wednesday, April 2, 2014
Security: Android Phone App Steals CPU
 |
| [Courtesy: AndroidAuthority ] |
Malware was seen traditionally only a Microsoft Windows problem. Now that highly secured, multi-platform, standards-based UNIX environments lose influence, malware continues to spread to poorly secured Linux environments. More importantly, Google Android's mobile phone and tablet platforms have fallen victim. Attacks continue mercilessly.
Recent History
Some recent Linux and Android validated attacks: January through November 2013, December 2013, January through February 2014, March 2014, and more malware is hitting the Linux and Android platforms. The most recent attacks are using your Linux based Android phones to create money for others.
Latest Attack
At the end of March 2014, a new attack was discovered... not only on the third-party Google Android application internet sources, but also multiple infected applications were found on Google Play.
2014-03-26 - Apps with millions of Google Play downloads covertly mine cryptocurrency
Yes, smartphones can generate digital coins, but at a painfully glacial pace.If you download applications from Google Play or other non-Google sites - you may be noticing terrible battery life, increased battery temperature, and increased network usage.
According to a blog post published Tuesday by a researcher from antivirus provider Trend Micro, the apps are Songs, installed from one million to five million times, and Prized, which was installed from 10,000 to 50,000 times. Neither the app descriptions nor their terms of service make clear that the apps subject Android devices to the compute-intensive process of mining, Trend Micro Mobile Threats Analyst Veo Zhang wrote. As of Wednesday afternoon, the apps were still available.
What This Means To You
While Google has managed to remove some trojan applications which were designed to steal CPU time from your smart phone in order to electronically harvest bit coins for application developers, there are others sitting in Google Play and in non-regulated application markets.
Wednesday, March 26, 2014
Security: Software Piracy, Android Phones, and SMS Spam
 |
| [Courtesy: Android Authority] |
Abstract:
Ever since the creation of computers, people have been distributing software to avoid paying money or paying to distribute something that people don't want. Pirated Applications and Spam are two primary means to distribute viruses, malware, and worms. Baby steps against these on-line monsters are occasionally made.
In Review: 2013
From January to November last year, nearly 2 viruses, trojans, or generic malware was discovered each month in the Android mobile application market. December had a couple more discovered. For the malware discovered, there are countless numbers of mobile applications which have not yet been discovered... to steal credit card information, identities, or even "command and control" applications to turn your mobile device into a robot against unsuspecting targets (while you pay for the data traffic that is produced!)
Starting: 2014
While consolidating a list of mobile malware in the Android market was not completed, it is clear that there is some progress in this space... no matter how small.
2014-03-25 U.S. Government First Convictions Over Pirated Mobile Android Applications
The US has enforced its first convictions for illegally distributing counterfeit mobile apps, after two Florida men pleaded guilty for their part in a scheme that sold pirated apps with a total retail value of more than $700,000. Thomas Allen Dye, 21, and 26-year-old Nicholas Anthony Narbone both pleaded guilty to the same charge - conspiracy to commit criminal copyright infringement - earlier this month and are due to be sentenced in June and July respectively. Both men were in the Appbucket group, of which Narbone was the leader, which made and sold more than a million copyrighted Android mobile apps through the group's alternative online market.
2014-03-26 Chinese Arrest 1,500 in Fake Cellular Tower Text Message Spam Raid
China’s police have arrested over 1,500 people on suspicion of using fake base stations to send out mobile SMS spam. The current crackdown, began in February, according to Reuters. Citing a Ministry of Public Security missive, the newswire says a group operating in north-east Liaoning province, bordering North Korea, is suspected of pinging out more than 200 million spam texts.
In Conclusion:
Be diligent! Remember to purchase your applications from reputable places, don't be seduced into stealing applications on-line or purchasing them under list price. Being a thief could make you a victim!
Tuesday, March 4, 2014
Security: Linux, Viruses, Malware, and Worms
 |
| [Huawei TP-Link image, courtesy rootatnasro] |
Hello everyone, I just wanted to discuss some vulnerability I found and exploited for GOODNESS .. just so that SCRIPT KIDIES won’t attack your home/business network .
Well, in Algeria the main ISP ( Algerie Telecom ) provide you with a router when you pay for an internet plan. So you can conclude that every subscriber is using that router . TD-W8951ND is one of them, I did some ip scanning and I found that every router is using ZYXEL embedded firmware.
 |
| [Linksys Router, courtesy ARS Technica] |
Linksys is aware of the malware called “The Moon” that has affected select older Linksys E-Series routers and select older Wireless-N access points and routers. The exploit to bypass the admin authentication used by the worm only works when the Remote Management Access feature is enabled. Linksys ships these products with the Remote Management Access feature turned off by default. Customers who have not enabled the Remote Management Access feature are not susceptible to this specific malware. Customers who have enabled the Remote Management Access feature can prevent further vulnerability to their network, by disabling the Remote Management Access feature and rebooting their router to remove the installed malware. Linksys will be working on the affected products with a firmware fix that is planned to be posted on our website in the coming weeks.
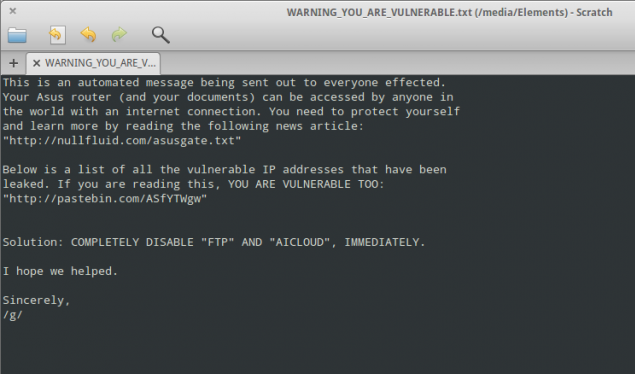 |
| [ASUS Warning, courtesy ARS Technica] |
"This is an automated message being sent out to everyone effected [sic]," the message, uploaded to his device without any login credentials, read. "Your Asus router (and your documents) can be accessed by anyone in the world with an Internet connection. You need to protect yourself and learn more by reading the following news article: http://nullfluid.com/asusgate.txt."
...
Two weeks ago, a group posted almost 13,000 IP addresses its members said hosted similarly vulnerable Asus routers.
Conclusions:
If you are doing any serious internet based work, one might suggest that care is taken to watch the firmware of your consumer grade internet router, and upgrade the firmware as they become available. If you are running a business, a commercial grade router with a managed service may be of special interest. A short PDF on "SOHO Pharming" helps clarify risks. The avoidance of Linux based Android phones or consumer grade Linux routers may be the next best step.
Monday, December 30, 2013
Security: A Linux Server Exploit
Why do people want to hack your server? Maybe it is to mine BITCOINS!
http://arstechnica.com/security/2013/12/anatomy-of-a-hack-what-a-successful-exploit-of-a-linux-server-looks-like/
Like most mainstream operating systems these days, fully patched installations of Linux provide a level of security that requires a fair amount of malicious hacking to overcome. Those assurances can be completely undone by a single unpatched application, as Andre' DiMino has demonstrated when he documented an Ubuntu machine in his lab being converted into a Bitcoin-mining, denial-of-service-spewing, vulnerability-exploiting hostage under the control of attackers.
Wednesday, July 17, 2013
North America: Wireless Network Carrier Update
Abstract:
Huge and significant changes are occurring in the Telecommunications and Wireless space during the month of July! Significant change in plans for consumers and consolidation of smaller-tier carriers may offer more competitive choice for consumers... but with advancements comes security risks.On the Mobile User front...
2013-07-10: T-Mobile’s new "Jump" service plan gives customers two upgrades per year
At a press conference in New York City Wednesday, T-Mobile unveiled a new type of mobile service plan that will allow customers to upgrade their phones up to twice a year with no outright financial penalty or waiting period. On the “Jump” plan, customers will still pay to switch phones, but they can get them at new-contract prices. Customers on T-Mobile will have to pay an extra $10 per month for the Jump plan.
2013-07-16: AT&T jumps on the frequent-phone-upgrade bandwagon with “AT&T Next”
Not to be outdone by T-Mobile's "Jump" program and Verizon's rumored "Edge" program, AT&T on Tuesday announced a plan called "AT&T Next" that will allow its customers to upgrade their smartphones and tablets more frequently without having to pay the full, unsubsidized price for the devices. AT&T Next gives customers the option to get a new phone or tablet with no down payment in exchange for an extra charge, equivalent to about five percent of the device's unsubsidized price, on their monthly bill.
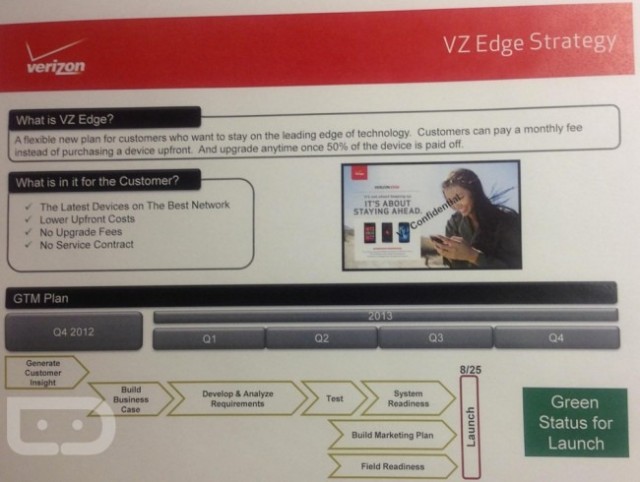
2013-07-15: Verizon’s rumored "Edge" plan may ensure you always have a new phone in your hands
It looks like the days of waiting two years for your next handset upgrade might be over. DroidLife is reporting that Verizon may be introducing its own “buy a new phone if you’re sick of your old one” plan later next month. According to the site’s source, the plan is called VZ Edge, and it will enable customers to upgrade their phones more often than once every two years to help them “stay on the leading edge of technology.”
On the Carrier front...
 |
| [AT&T storefront, courtesy Business Insider] |
As a way to solidify its spectrum holdings and gain a stronger foothold in the growing prepaid mobile market, AT&T has agreed to acquire Leap Wireless (and its prepaid Cricket brand) for $15 per share, which works out to $1.1 billion, given 79.05 million in outstanding shares. Considering that Leap’s closing stock price on Friday afternoon was $7.98 per share, that’s a hefty premium. ... As of April 15, 2013, Leap had $2.8 billion of net debt. Leap shareholders will also receive a contingent right entitling them to the net proceeds received on the sale of Leap’s 700 MHz ‘A Block’ spectrum in Chicago, which Leap purchased for $204 million in August 2012.”
2013-07-05: FCC clears way for SoftBank to buy Sprint, Sprint to buy Clearwire
The U.S. Federal Communications Commission on Friday announced the removal of the last barrier to a three-company merger that will see Japan's SoftBank take control of Sprint Wireless, which itself is set to take over Clearwire.
2013-07-10: SoftBank priority is beefing up Sprint, not exec changes
SoftBank Corp (9984.T) will move rapidly to use airwaves from Clearwire Corp CLWR.O to bolster Sprint Nextel Corp's (S.N) wireless service, but it does not plan any big personnel changes once it takes over the No. 3 U.S. mobile carrier, a top SoftBank executive told Reuters.2013-07-11: Sprint wants to become the mobile autobahn, removes all limits for life
Sprint has thrown down its own gauntlet in attracting...(e.g., contract) customers: guaranteed unlimited voice, text, and data, forever. In a press release Thursday, Sprint said that this deal would apply to both new and existing customers who sign up for Sprint’s new Unlimited, My Way, or My All-In plans. The deal will be available starting Friday, July 12, 2013 for just $80 per month.
On the Hardware front...
 |
| [image courtesy article on femtocells from gigaom.com] |
Security researchers have demonstrated a flaw in femtocells that allows them to be used for eavesdropping on cellphone, email, and internet traffic. The hack was demonstrated on Verizon hardware, and the telco giant has issued an update to patch the vulnerability, but up to 30 other network carriers use systems with software that can be hacked in the same way. Femtocells are used to boost Wi-Fi and mobile signals within a household, but a common form of software that many devices use has a major security flaw that allows all traffic to be recorded and analyzed.
Tuesday, January 15, 2013
DefenseCode: Linksys 0 Day Vulnerability
Security professionals DefenseCode identified a security vulnerability in Linksys router software, which allows people to achieve privileged command line access without authentication. There is no known patch, at this point, to thwart the exploit.
Whose Talking:
The exploit has been reported inTech/Science news like The Register and Slash-Dot and Net-Security and
It appears the exploit.
A Register User quotes DefenseCode CEO Leon Juranicvor regarding internet vulnerability:
We're still investigating some tricks to exploit this vulnerability from the internet, but for now, yes - it seems safe from the outside of the network. Of course, unless services are available from the internetCisco has responded to The Register:
"Linksys takes the security of our products and customers’ home networks very seriously. Although we can confirm contact with DefenseCode, we have no new vulnerability information to share with customers – for our WRT54GL or other home routers. We will continue to review new information that comes to light and will provide customer updates as appropriate."Cisco has responded, according to Net-Security:
After the researchers posted their findings online, Cisco finally got in touch again. They are expected to release a fix in time for the full advisory, which should see the light of day in about 10 days.There is a vulnerability, a patch is coming, and everyone knows about it. Implications: If you are a Network Operations Center, keep an eye out for the patches coming from Cisco/Linksys and get ready for a huge patch software automation. If you do not have Network Management service with a vendor, you should consider such a service for times such as these.
Monday, December 24, 2012
Security: 2012 December Update
Microsoft Windows Security Update Breaks Fonts... Update 2753842 Root Cause...
Breaking Windows Passwords in under 6 hours...
New "Dexter" Malware Infects Microsoft Point of Sale Systems to Steal Credit Cards...
Distributed Denial of Service Attacker Anonymous on the Run...
The Pakistan Cyber Army Attacks Chinese and Bangladeshi Web Sites...
ITU: Deep Packet Snooping Standard Leak...
Democrats and Republicans Unite Against ITU Internet Control...
Industrial HVAC systems targeted by hackers...
Microsoft Internet Explorer watching you, even when not open on your screen!
Android Malware Trojan Taints US Mobiles, Spews 500,000 Texts A Day!
Baby got .BAT: Old-school malware terrifies Iran with del *.*; dubbed BatchWiper; found 7 months after Flame discovery
Apple Shifts iTunes to HTTPS, Sidesteps China’s Firewall
Christopher Chaney, Scarlett Johansson's e-mail hacker, sentenced to 10 years
Friday, April 13, 2012
Zero-Day Exploit: WICD under Linux

This has been a bad week for computing systems.
- Oracle Java exploit under Apple MacOSX, open and shut case.
- Microsoft Zero-Day Exploit in nearly all applications, still somewhat open.
- Adobe Acrobat Reader (Windows, MacOSX and Linux), open and shut case.
- Now a Linux Security issue, open and shut case.
As published in the patch description.
Backtrack 5 R2 (the latest version) allowed the student to overwrite settings to gain a root shell. The flaw was found in wicd (the WirelessWhat is WICD?
Interface Connection Daemon)
A network connection manager that aims to simplify wired and wireless networking in Linux.If you are a wireless Linux user of WICD, get your patch.
Monday, February 13, 2012
Vonage and MSN Port Usage
Vonage and MSN Port Usage
Abstract:
Adding Voice over IP (VoIP) and Instant Messaging to a home is normally a simple process. The goal is often to increase communication while reducing telecommunications bills. Occasionally, there are problems with access, which required troubleshooting or more advanced features are desired. A user may need to understand the protocols, in order to better maintain security, and limit scope to attacks by viruses and worms.Vonage Voice Adapters
Service | TCP | UDP | Notes |
DNS | 53 | Name Resolution | |
TFTP | 21,69,2400 | Firmware Upgrade | |
HTTP | 80 | Configuration | |
SIP | 5061 | pre-2005 Vonage devices | |
RTP | 10000-20000 | RTP (Voice) traffic |
When a call is made, a random port between 10000 and 20000 is used for RTP (Voice) traffic. If any of these ports are blocked, you may experience one way or no audio.
Microsoft MSN and Windows Messenger
Service | TCP | UDP | Notes |
Windows Messenger - voice | 2001 - 2120 6801, 6901 | Computer to Phone | |
MSN Messenger - file transfers | 6891 - 6900 | Allows up to 10 simultaneous transfers | |
MSN Messenger - voice | 6901 | 6901 | Voice communications computer to computer. |
MSN Messenger text | 1863 | Instant text messages |
The ports may be helpful when you want to limit vulnerabilities within your environment to unfriendly viruses and worms.
Monday, April 25, 2011
X Windows: XRECORD Extension

X Windows: XRECORD Extension
Abstract:
The X Windows XRECORD Extension allows for a free framework to observe and record graphical activities of an X Windows client program running on an X Server. The XRecord extension may have been released with X11 release 6.1, although documentation was released from with X11 release 6.4. The extenions may be leveraged for security purposes (i.e. auditing), careful watching of an X Server for smoother remote frame buffer implementations, or even for automating testing procedures.
Definition:
[html | pdf] --- XRecord Extension Library - Version 1.13 - X Consortium Standard - X Version 11, Release 6.4 - Copyright © 1994 Network Computing Devices, Inc - Copyright © 1995 X Consortium
Example Uses:
[html | pdf] --- Version 0.7.2beta of x11vnc - The X RECORD extension is used to detect some scrolls.
[html | pdf] --- PyKeylogger is a free open source keylogger written in the python
[html | pdf] --- Xnee is a suite of programs that can record, replay and distribute user actions under the X11 environment. Think of it as a robot that can imitate the job you just did.
[html | pdf] --- AutoKey is a desktop automation utility for Linux and X11. It allows you to manage collection of scripts, and assign abbreviations and hotkeys to these scripts allowing you to execute them on demand in whatever program you are using.
[html | pdf] --- Issues in Fedora 10
[html | pdf] --- X RECORD extension C Code example.
[html | pdf] --- Record keystrokes via Per module.
[html | pdf] --- Apple MacOSX vnc2swf to record vnc and aqua sessions.
[html | pdf] --- vnc2swf, to record vnc sessions in macromedia shockwave files.
[html | pdf] --- vnc2flv, to record vnc sessions in adobe flash files.
[html | pdf] --- screencasting under Solaris.
[html | pdf] --- How to Create a Flash Demo using Vnc2swf.
[html | pdf] --- Recording your screen in Solaris works right out of the box. All you need to install is vncserver and vnc2swf.
Commercial Uses:
[html | pdf ] --- The Pose technology is used for exactly and totally recording (capture) and later or simultaneous playback of X11 sessions or individual applications, optionally together with audio, video, or arbitrary binary data streams. The recording may be converted to video formats
Thursday, March 24, 2011
2011 March 20-36: Articles of Interest
2011-03-16 - Microsoft malware removal tool takes out Public Enemy No. 4
Microsoft finally used its Malicious Software Removal Tool to remove the fourth-biggest threat in automated program's history dating back to at least 2005.
2011-03-18 - RSA breach leaks data for hacking SecurID tokens
'Extremely sophisicated' attack targets 2-factor auth
2011-03-20 - AT&T acquires T-Mobile USA from Deutsche Telekom for $39bn
There was one GSM network, to rule them all...
2011-03-23 - Mac OS X daddy quits Apple
Bertrand Serlet, Apple’s senior vice president of Mac software engineering and the man who played a lead role in the development of Mac OS X, is leaving the company.
2011-03-23 - 'Iranian' attackers forge Google's Gmail credentials
Skype, Microsoft, Yahoo, Mozilla also targeted.
Extremely sophisticated hackers, possibly from the Iranian government or another state-sponsored actor, broke into the servers of a web authentication authority and counterfeited certificates for Google mail and six other sensitive addresses, the CEO of Comodo said
2011-03-23 - Oracle announced all software development stopped on Intel's Itanium CPU.
Red Hat was the first to pull the plug on Itanium, saying back in December 2009 that its Enterprise Linux 6 operating system, which was released last summer, would not be supported on Itanium processors.
Microsoft followed suit in April 2010, saying that Windows Server 2008 R2 and SQL Server 2008 R2 would be the final releases supported on Itanium.
2011-03-24 - Apple Mac OS X: ten years old today
OS X was the product of Apple's 1996 purchase of NeXT, a move that not only saw the acquisition of a modern operating system, but also the return of its co-founder, Steve Jobs, to the company.
Thursday, March 10, 2011
Security: Taret: Linux Network Devices

Security: Target: Linux Network Devices Abstract:
Widespread use of Microsoft operating systems on the desktop and server have been increasingly exploited by malware for dubious uses. The ever growing increased use of Linux on low-end network devices have made an interesting target for malware creators. Most recently, attacks using compromised Microsoft platforms have been targeting low-end Linux network devices.
History:
Malware, which cooperates with one another over the internet have been called Botnets. They have taken over Microsoft PC's and Servers, because of their ubiquitousness, across the globe. They can be very difficult to find and destroyed, as demonstrated by the Kneber botnet. First known activity for Kneber dates back to March 2009.
As the popularity of Linux grew, the movement of malware from Microsoft platforms to Linux platforms began
In January 2008, a DNS attack on DSL modems was discovered in Mexico. The 2Wire DSL modems were targeted, re-directing people from a Mexico bank to a site falsely demonstrating itself to be a bank.
In January 2009, the Psyb0t was discovered, targeting MIPS based Linux devices.
In February 2010, the Chuck Norris Botnet targeted D-Link Linux based devices.
Sometimes, the network devices are merely used to perform distributed denial of service attacks against corporations or entire nations, as what is happening in South Korea during March 2011.
These botnets are dangerous and could be used to infiltrate other devices on a network, which are then used to gather information, for the purpose of theft or other illegal nefarious behavior.
Enter: Elf_Tsunami.R
In March 2010, a new exploit has been discovered. Elf_Tsunami.R was uncovered by TrandLab. The D-Link DWL-900AP+ is vulnerable, as well as other devices. Formerly exploited Microsoft systems infected with malware can attack and infiltrate the Linux network devices on the local area network.
Elf_Tsunami.R leverages Internet Relay Check (IRC) servers as an independent transport, after the Linux network device is infiltrated, meaning PC anti-virus software can not completely clean out your network, after cleaning your PC.
Network Management Connection:
It has long been expected that Linux would remain more secure to attacks, over Microsoft based appliances, desktops, and servers. Linux consumer based devices, however, are widely available and do not necessarily meet the stringent security requirements for Enterprise and Managed Services networking infrastructure.
Caution should be taken when employing Microsoft and Linux platforms in an Enterprise and Managed Services networking infrastructure, because of the increased use of hybrid exploits. The possibility of infecting customer networks through their implementation is not out of the question, as demonstrated by millions of globally exploited systems and devices.
Saturday, September 18, 2010
Linux: Root Exploit Briefly Closed Finally Resolved

Security Alert - Upgrade Linux Systems Again...
Another Linux root exploit found last decade, briefly closed for a few months, has finally been closed.
The Linux kernel has been purged of a bug that gave root access to untrusted users – again.
The vulnerability in a component of the operating system that translates values from 64 bits to 32 bits (and vice versa) was fixed once before – in 2007 with the release of version 2.6.22.7. But several months later, developers inadvertently rolled back the change, once again leaving the OS open to attacks that allow unprivileged users to gain full root access.
There are a lot of production systems which have been compromised by this defect over the past half-decade.
Network ManagementLet's hope that affected systems are not runnning mission critical systems in your managed services environment that connect to tens of thousands of customer devices in a Network Management environment. It means another hit on availability and taking down the systems for yet another upgrade.
Friday, August 20, 2010
McAfee: Purchased by Intel After Fiasco

McAfee: Purchased by Intel After Fiasco
What is Virus Protection?
Operating Systems like Microsoft Windows offers mechanisms to install software automatically. Sometimes, it the mechanism is a bug. Other times, it is a key which may have been purchased or hacked, and later leveraged to deposit viruses or spy-ware. Sometimes, the OS just offers too much freedom to the user, to allow them to install anything they would like (anywhere they would like), and when they unwittingly install a piece of software on purpose, the machine becomes infected.
Some consider it the computing system equivalent to the Mafia, "You want to be safe, pay us some protection money, and you'll be safe." They work to make the computing environment more rigid because the operating system vendor (in this case, Microsoft) was too lazy.
To make the environment more rigid, inspection is done for known snips of code on files loaded on the hard drive, coming in or out via email, or through tools like web browsers. These pieces of code that are searched for, basically subets of the possible virus or worms which can be used to identify them, are called "signatures".
The "signatures" are distributed from central locations from the Mafia's God Father to the software applications which some people choose to install on their computer, hereafter referred to as the Hitman. It is the job of the Hitman on your computer to whack the virus... or regularly encourage you to pay-up if you did not pay your security bill.
Leading up to the Acquisition:
Less than half a year ago, McAfee distributed a virus signature update that identified a core Microsoft Windows file a problem and whacked it.
McAfee update crippled some Windows PCs by quarantining or deleting a file crucial to Windows operation, called “svchost.dll”.Large segments of society, especially emergency services who were unfortunate enough to pick Microsoft Windows for their core infrastructure, in combination with McAfee, and various service packs were scrambling for cover.
The bug, McAfee said, meant that “less than half of one per cent” of business customers, and a smaller number of consumer customers, could not use their computers. The company did not release any detailed figures, but said that the problem nly occurred on machine running Windows XP Service Pack 3 in combination with a specific build of McAfee’s antivirus product.
Reported victims include Kansas City Police Department and and the University of Kansas Hospital and about a third of the hospitals in Rhode Island. PCs also went haywire at Intel, the New York Times reports, citing Twitter updates from workers at the chip giant as a source.McAfee picked up very bad reputation after this event.First hand experiences from an Iowa community emergency response centre, ironically running a disaster recovery exercise at the time, can be found in a posting to the Internet Storm Centre here. The Register has heard from a senior security officer at a net infrastructure firm that was also hard hit by the snafu, as reported in our earlier story here.
To be fair, a virus signature is nothing more than a pattern of bits that can appear in a file at a particular set of locations, so it is amazing that after all these years, with so many virus signature creators, that this has not happened earlier.
The New God Father:
After a very bad spring and summer, the cost of the help desk support to repair all of those old machines, lost customers who would stop using their products, bad media coverage from the mishap, and new customers who were not very interested in taking a chance on them - someone else was really needed to clean up their reputation.
Intel Corporation made purchased McAfee. What surprises me is that fewer media outlets had connected the purchase with the recent virus signature failure.
Network Management Connection:
Microsoft Windows systems are tremendous targets for viruses and worms. With Network Management systems which must be located in a DMZ and connect to millions of potential end points, such platforms should be considered a virus & worm distribution system, and avoided.
The application of virus definitions to such production systems can disrupt the reputation of a third party management company and put them out of business, the same way McAfee tarnished reputation needed to be consumed by Intel.
Linux: 5 Year Old Root Exploit Finally Patched

Security Focus:
It has been a over half decade, but a Linux kernel root exploit has finally been patched. Yes, Oracle Enterprise Linux, RedHat, and others have been running around with this issue for a long time.

For your Novell fans, the SUSE distribution has been OK since 2004, but it has not trickled down to the other distributions since the fix had not been incorporated into the official kernel until now.
Network Management:
In a world of network management where a central or even distributed systems monitor or manage millions of potential device across many thousands of networks, a root exploit in an operating system kernel dating back over a half decade is extremely high risk.
If it has to run and has to run securely - a generic Linux distribution may not fit the bill.
Look for Operating System vendors who have a strong record with understanding Data Centers and managing networks, not just OS vendors who can do it more cheaply.