Inevitable: Apple MacOSX Infected via Java on Web
Abstract:
Desktop and Server based systems based upon Microsoft Windows platform have long been the most vulnerable platforms on the internet, providing the most efficient platform for malware writers to steal computing and network cycles from owners around the world. Various other open platforms (i.e. UNIX based systems), which serves much of the internet traffic, have long tried to keep from being infected, by applying more rigorous security rules at the OS level. Apple, being one such vendor who migrated to a UNIX platform, had been successful in keeping their clients secure - but finally a single Java based vulnerability has been discovered (and leveraged) to exploit some systems.
Virus Buster:
A virus vendor located in Russia recently published a short research article on a particular threat, which has been closed by Apple.
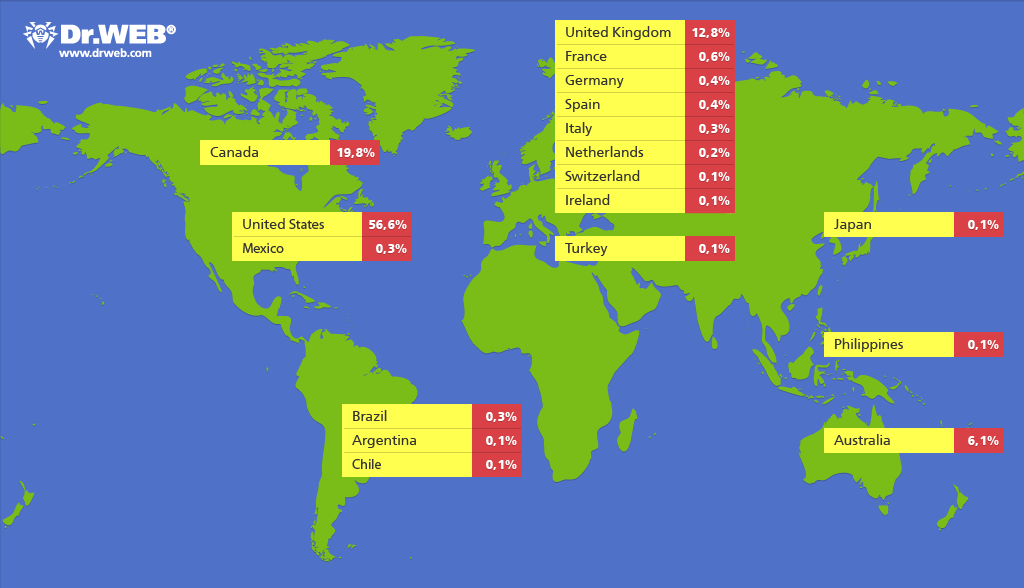
Doctor Web—the Russian anti-virus vendor—conducted a research to determine the scale of spreading of Trojan BackDoor.Flashback that infects computers running Mac OS X. Now BackDoor.Flashback botnet encompasses more than 550 000 infected machines, most of which are located in the United States and Canada. This once again refutes claims by some experts that there are no cyber-threats to Mac OS X.While very uncommon, MacOSX based Apple Macintosh computers occasionally have third-party based software (i.e. Flash, Java, etc.) which can offer some level of vulnerability to all platforms, including MacOS, Windows, UNIX, etc.
The Origin:
The virus research company explains how computers get infected.
According to some sources, links to more than four million compromised web-pages could be found on a Google SERP at the end of March. In addition, some posts on Apple user forums described cases of infection by BackDoor.Flashback.39 when visiting dlink.com.The Morphing:
Companies started working on a solution, but before Apple released a patch, there was an attempt to diversify the virus, so they might be able to survive once it was closed.
Attackers began to exploit CVE-2011-3544 and CVE-2008-5353 vulnerabilities to spread malware in February 2012, and after March 16 they switched to another exploit (CVE-2012-0507).Security, At Last:
While this vulnerability has been "in the wild" on the internet for awhile, this particular virus was exterminated.
The vulnerability has been closed by Apple only on April 3, 2012.Protecting Yourself:
This particular threat is not unique to Apple, but also other systems like Windows. Apple released a security patch, to close this vulnerability - it would be well advised that you regularly download updates from Apple to apply these patches whenever possible.
A general rule of thumb: STAY AWAY FROM IMMORAL (i.e. pornography) AND ILLEGAL (i.e. copyrighted material like music, videos, software, etc.) DOWNLOADS - NEVER VIEW OR DOWNLOAD SOFTWARE OFF OF THE INTERNET, UNLESS IT IS A WELL KNOWN SITE - NO MATTER WHAT COMPUTER YOU ARE ON... these sites notoriously try to download viruses to your computer!
Apple has applied the proverbial "hammer" to this virus/trojan - disable Java unless explicitly requested by the user, and re-disable it if the user requests it over 30 days previous.
ReplyDeletehttp://support.apple.com/kb/HT5242