Online Forum
Oracle Solaris 11:
What's New Since the Launch
April 2012
Session I - Keynote: Oracle Solaris Strategy and Update
Abstract:
Markus Flierl, Vice President, Oracle Solaris Engineering, delivered the keynote - the first 1 hour session of 4 sessions on Oracle Solaris 11: What's New Since the Launch. From the entire first session, several major enhancements were noted in Solaris 11 Update 1:
- Solaris 11 Update 1 - re-architecture of virtual memory sub-system
New systems coming with 64 sockets, 64 terabytes of main memory - Solaris 11 Update 1 improves python performance
30% performance improvement - Solaris 11 Update 1 improvement in network system
Link aggregation across multiple switches
Improve ability to migrate VNIC configuration across to new system - Solaris 11 Update 1 Due in late 2012
To co-inside with other SPARC and Intel releases

Over the last 6 months
- SPARC T4 Support
(Some customers seeing 5-7x improvement in single thread improvement)
- Working on T5 in Lab
- Release Solaris 11
- SPARC SuperCluster
- Solaris Cluster 4.0
- Oracle Studio 12
- Oracle Enterprise Manager Ops Center 12c

Review
- #1 UNIX
- Solaris 11 Update 1 to be released end of 2012
- First "Cloud" OS
Satisfy traditional customer requirements for: availability, security, performance, scalability
- Shipped new network stack
Scale to 40GBit via parallel pipes

Simplified Administration
- 3x faster provisioning over VMWare
- 4x faster upgrades over Red Hat
- 2.5x faster reboots over Red Hat
- 46% fewer hardware outages using FMA
- Designed-in Virtualization
- Scalable Data Management
- Advanced Protection
New availability
- Preparing to implement K-Splice under Solaris

Designed-in Virtualization
- Fully virualized
OS, Network, and Storage
- Virtual Network Services built-in
- 15x better overhead efficiency over VMWare
- 4x Lower Latency over KVM

Scalable Data Management
- 10x storage savings for virtualization
- 2x storage compression
- 2x SPC-1 IOPS at 1/2 cost over NetApp

Advanced Protection / Security
- Immutable root file system
- 4.3x faster OpenSSL over AIX
- 3x faster ZFS encryption on SPARC over Westmere x86
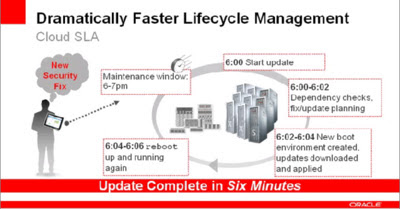
Dramatically Faster Lifecycle Management
- Apply security fixes in minutes, during maintenance window, with fast reboot
- KSplice technology being actively investigated, to enable hot-patching
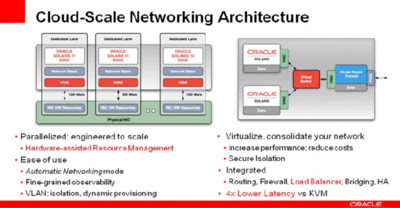
Cloud-Scale Networking Architecture
- Link aggregation across multiple switches
- vnic migration to new environment
- Hardware assisted resource management
- vlan: isolation & dynamic provisioning
- integrated: routing, firewall, load balancer, bridging, HA
- 4x lower latency over KVM

ZFS Virtualized Pooled Storage
- Scale out design. Built-in data services
- flash enabled virtual pools
- compression
- replication
- deduplication
- dataset encryption
- 10x dedup in virtualized environments
- rapid provisioning of virtualized storage resources (zfs snapshots, clones)
- no silent data corruption, ever

Oracle's Complete Cloud Management
- Self Service, provisioning
- billing for chargeback
- included in the base price of Solaris, if support

#1 UNIX. Engineered for Oracle
- Best of breed components
- Co-engineeered with Apps and hardware
- Unique value in engineered systems
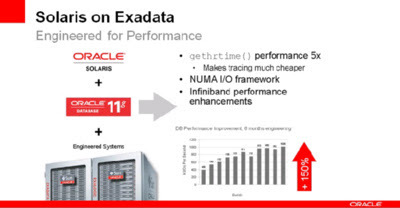
Solaris on Exadata
- Performance from 400K IOPS to over 1 Million IOPS
- Enabling Zones under Exadata and SuperCluster, to allow customers to carve out the machines for public and private cloud services

Java 7 Performance Trends
- 2.2x improvement through JDK 7 development through tuning
- Java 7 Update 4 supports crypto hardware
- Java 7 Update 4 Solaris 4x-5x crypto performance improvement
- Java mission control, debugging leveraging dtrace
- Solaris Scheduler tuning for JVM

SPARC Future Work
- crypto speed enhancement
- oracle number enhancement
- memory versioning
- 3x-5x improvement

Solaris: Engine for ZFS Storage Appliance
- Best Performance - 2x faster than NetApp
- Best Efficiency - best analytics
- Best Quality - #1 Storage Magazine
- Best for Oracle Software - engineered together
Used in Exadata, preferred backup solution for Exadata

Roadmap - Accelerating Investment
- Solaris 11 Express end of 2010
- Solaris 11 shipped end of 2011
- Solaris 11 Update 1 targeting end of 2012
- Solaris 12 requirements on the horizon
- SPARC T5 and M4 based systems in the lab
- Intel Sandy Bridge announcement on April 10
(The dates on the roadmap and positioning of technologies do not line up)